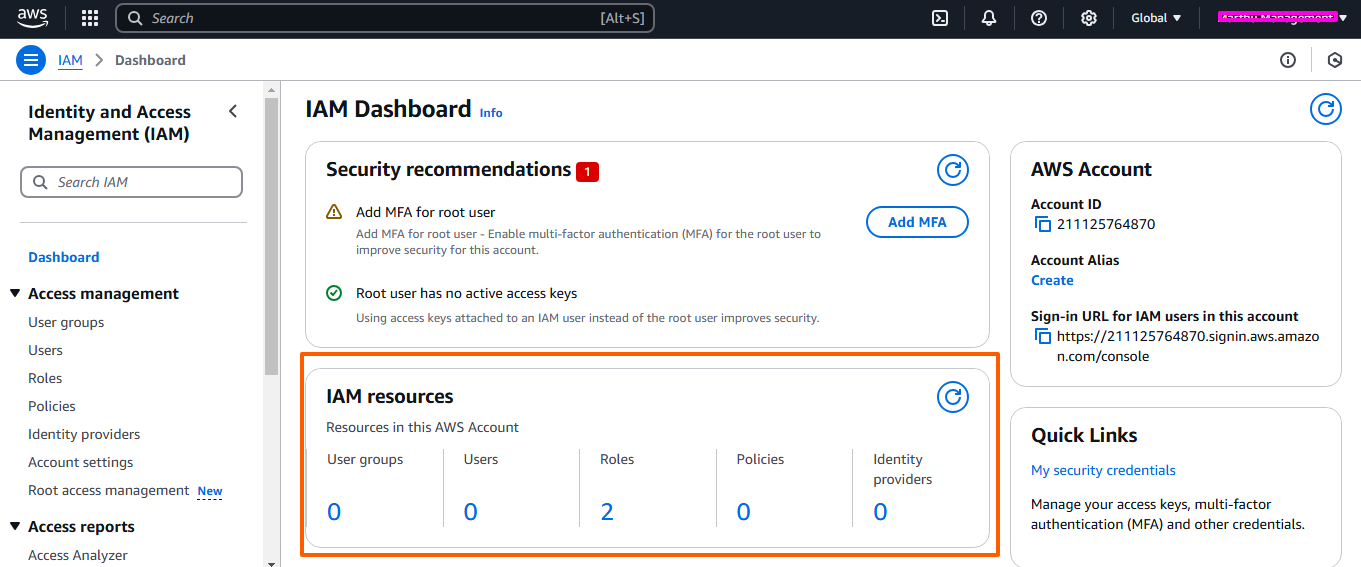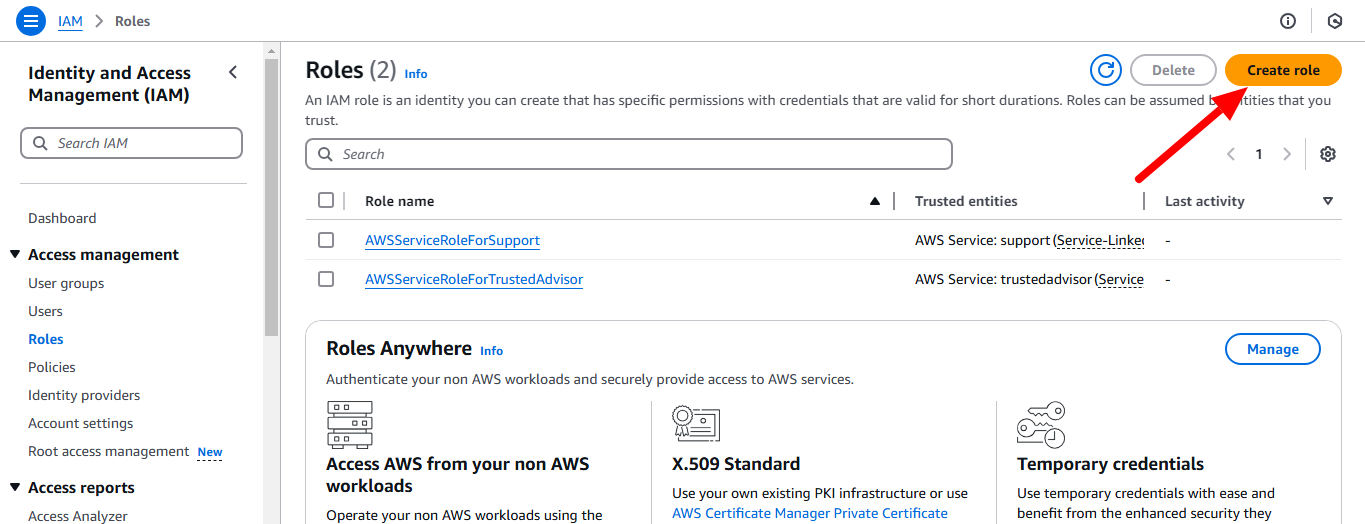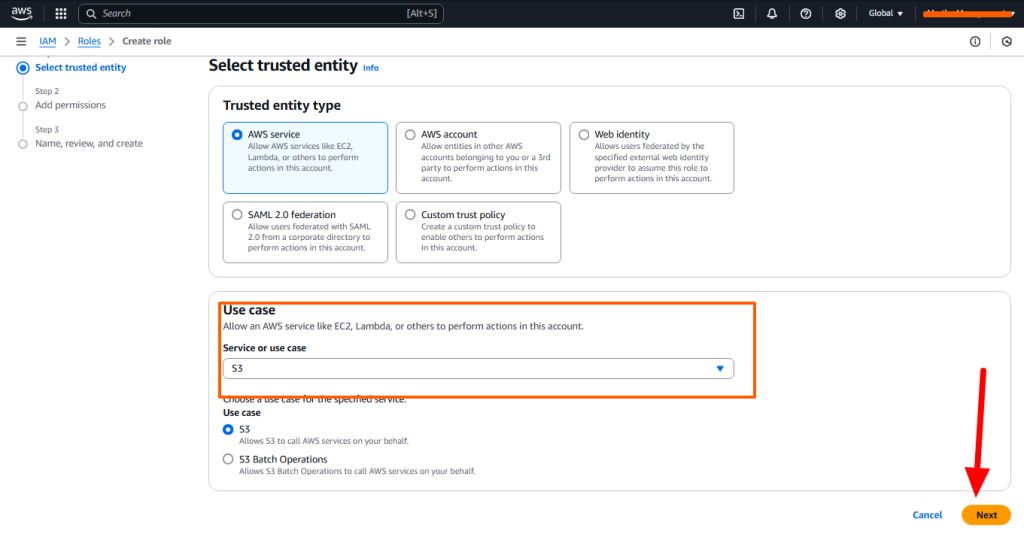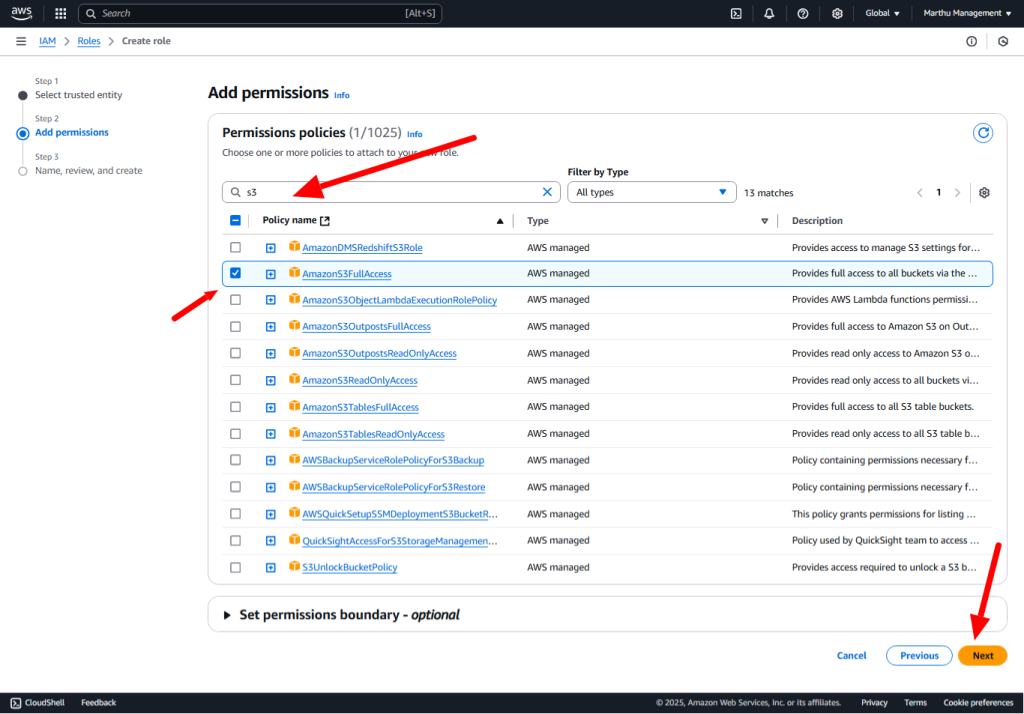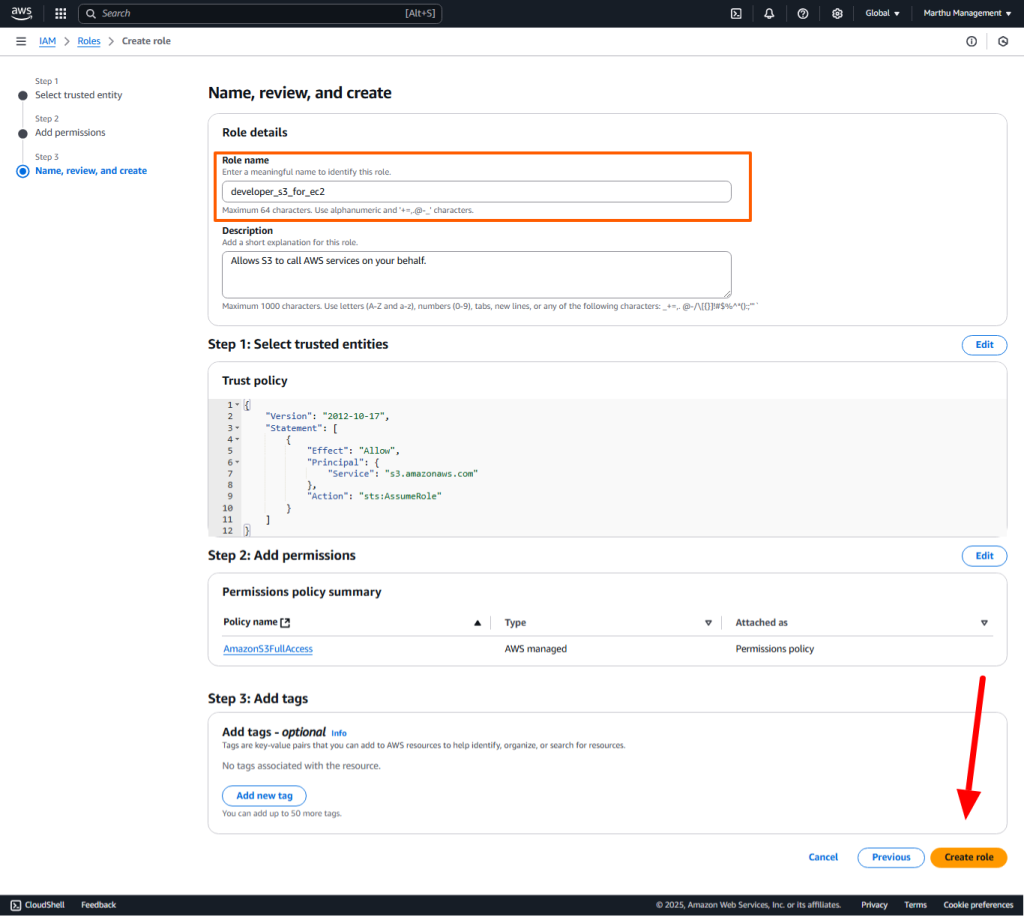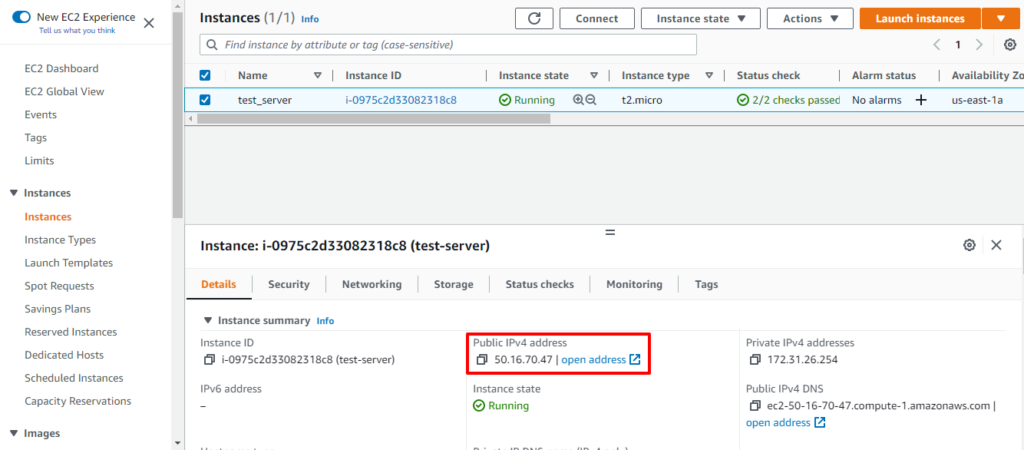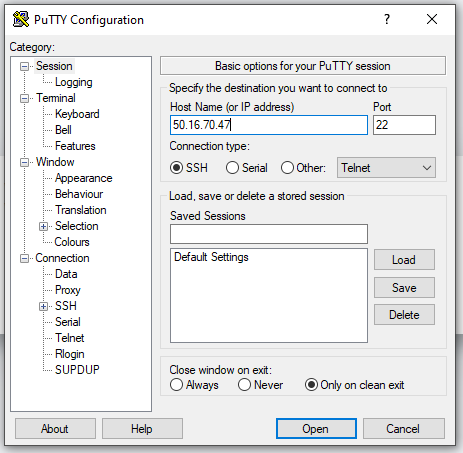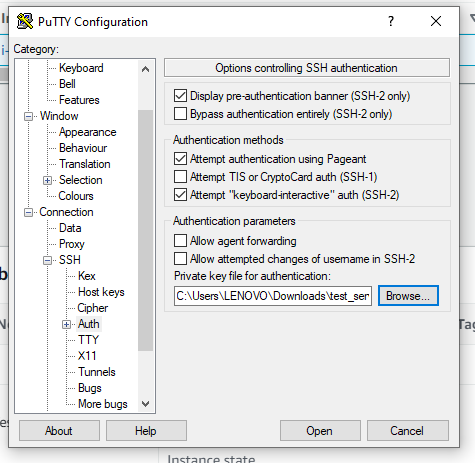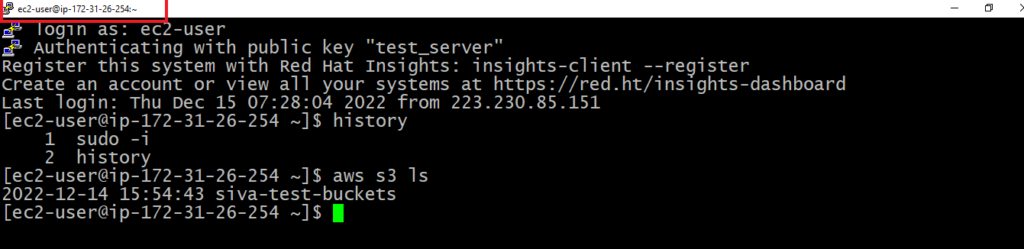
AWS IAM is one of the most powerful and important services enabling secure access management to AWS services and resources. With AWS IAM, we can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources.
Let’s look at some of the key features that make IAM so versatile and powerful:
Authentication or identity management in AWS IAM consists of the following identities:
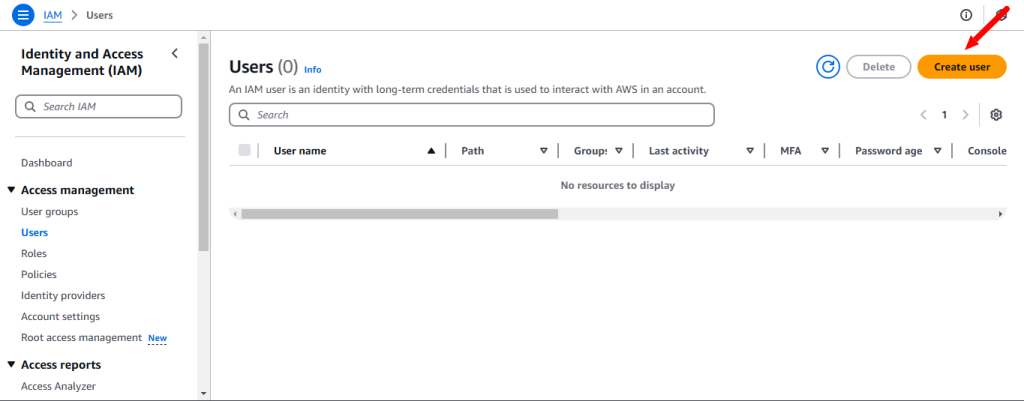
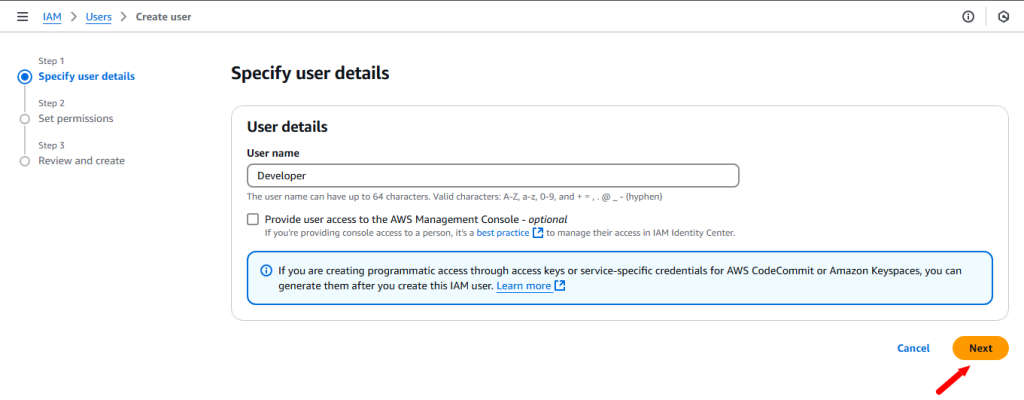
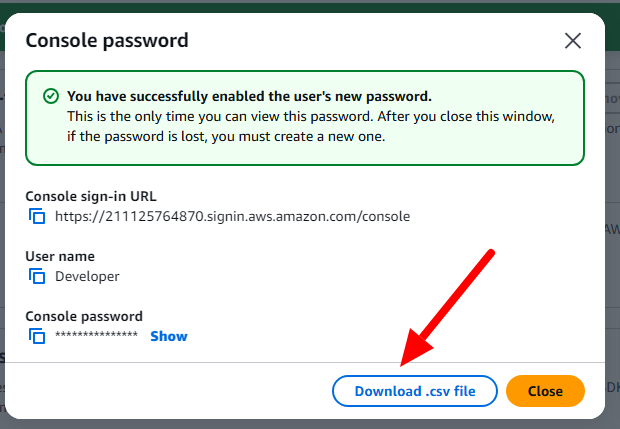
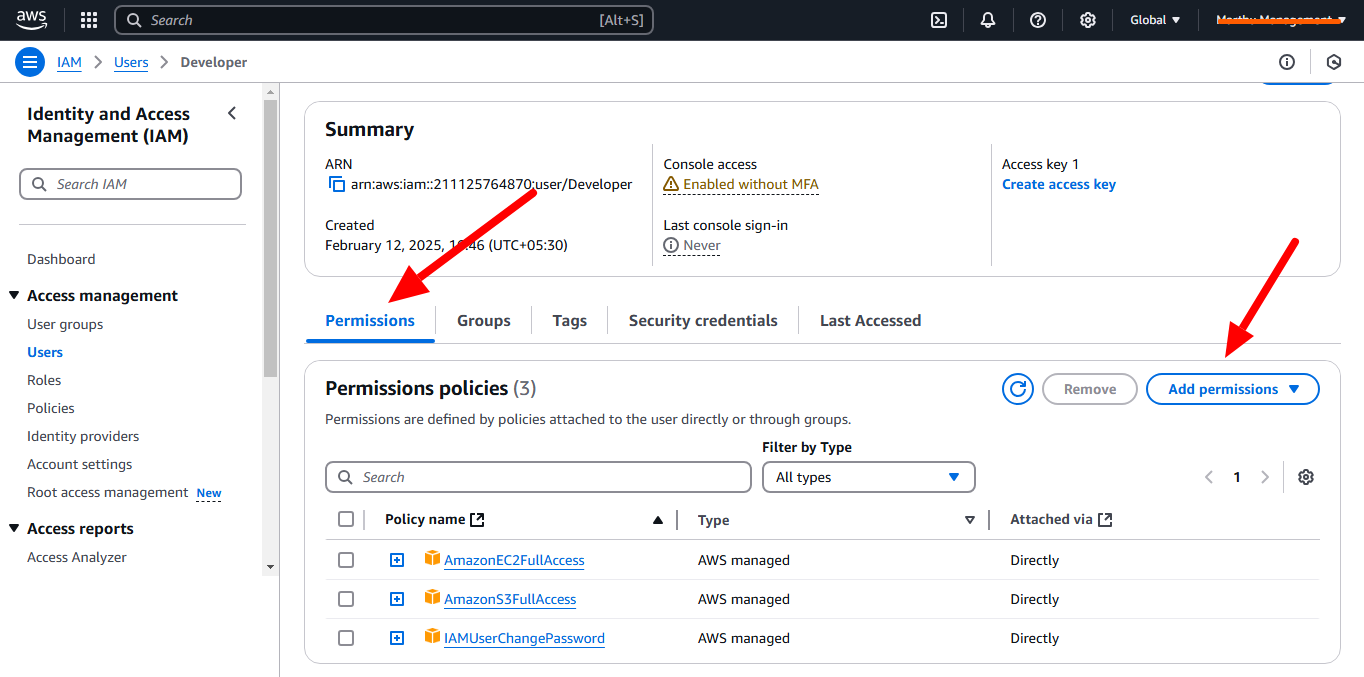
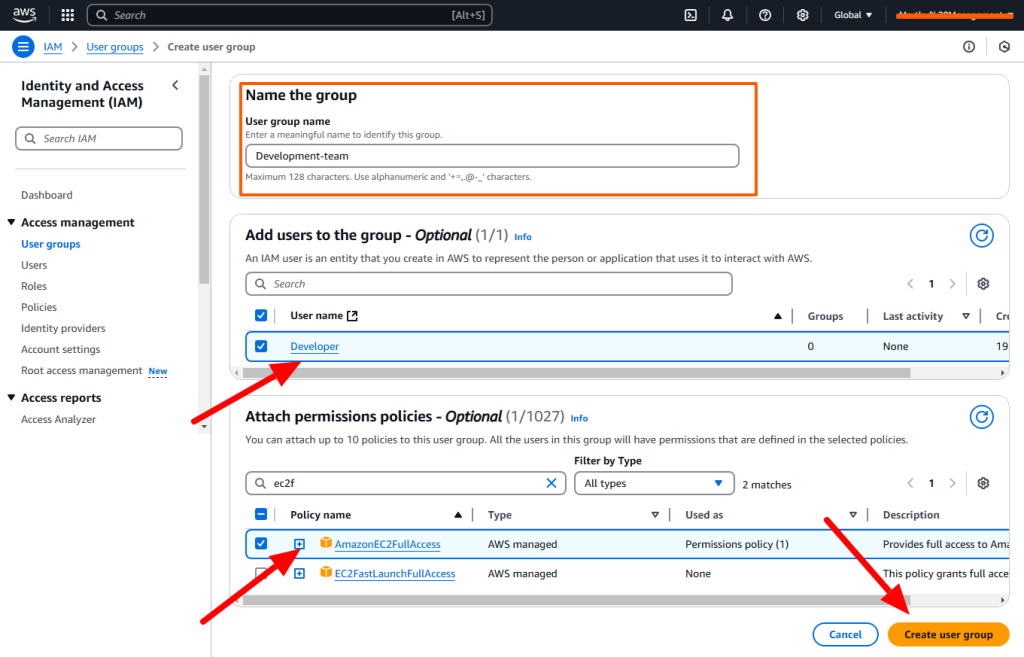
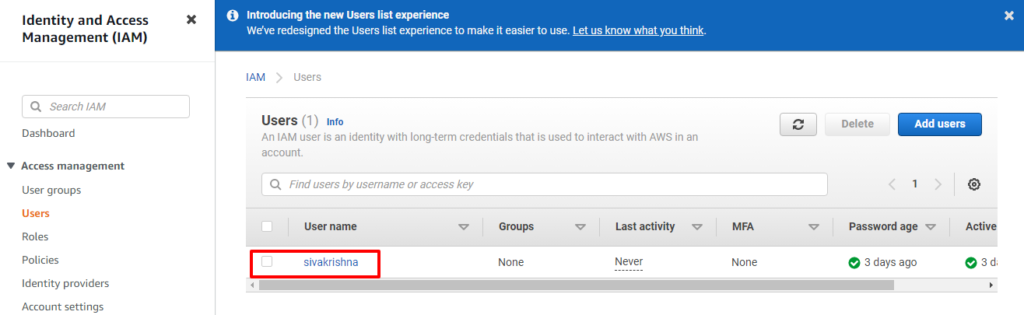
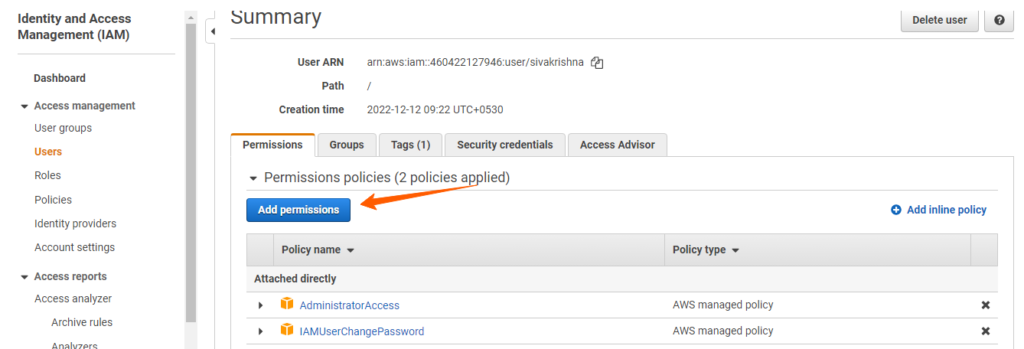
Users: An IAM user is a user who can have the access to our console resources with username & password having permenent Access key & Secretkey.
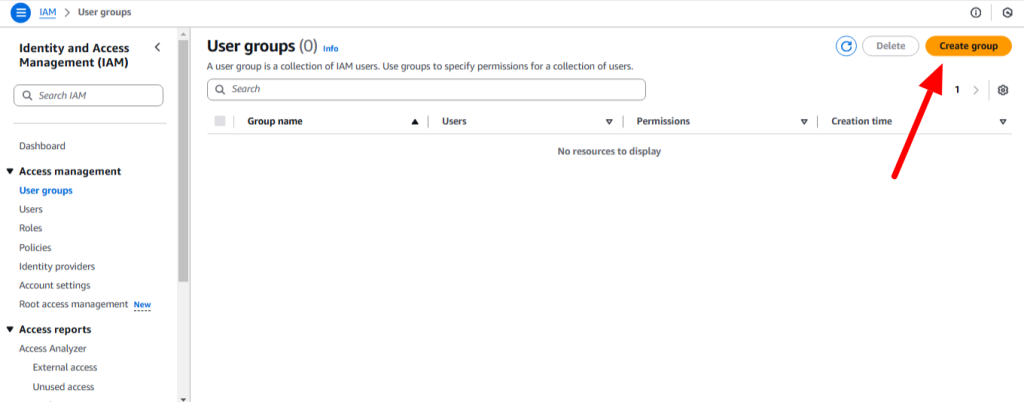
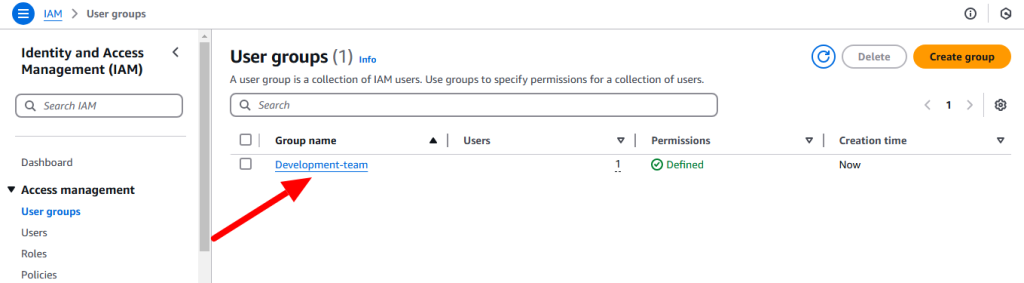
Groups: An IAM group is a collection of IAM users. You can organize IAM users into IAM groups and attach access control policies to a group. A user can belong to multiple groups. Groups cannot belong to other groups.
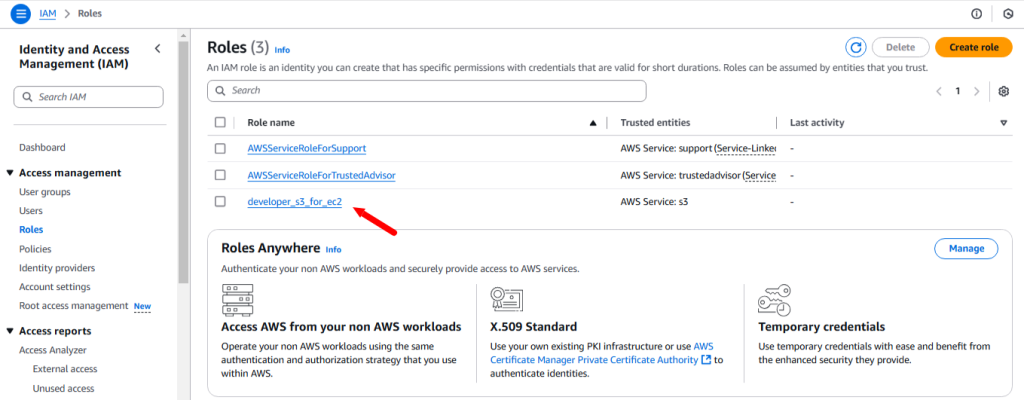
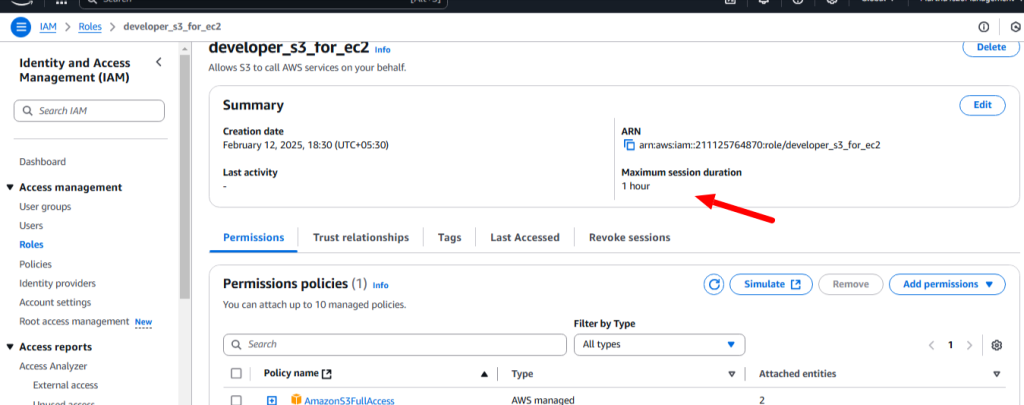
Role: Communication between the different services using the role. A role does not have any credentials associated with it. An IAM user can assume a role to temporarily take on different permissions for a specific task.
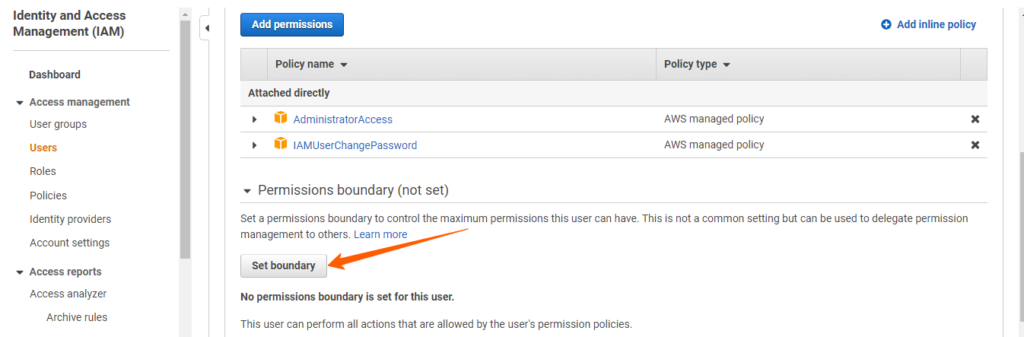
Authorization or access management in IAM is gives those users permission to access a resource.
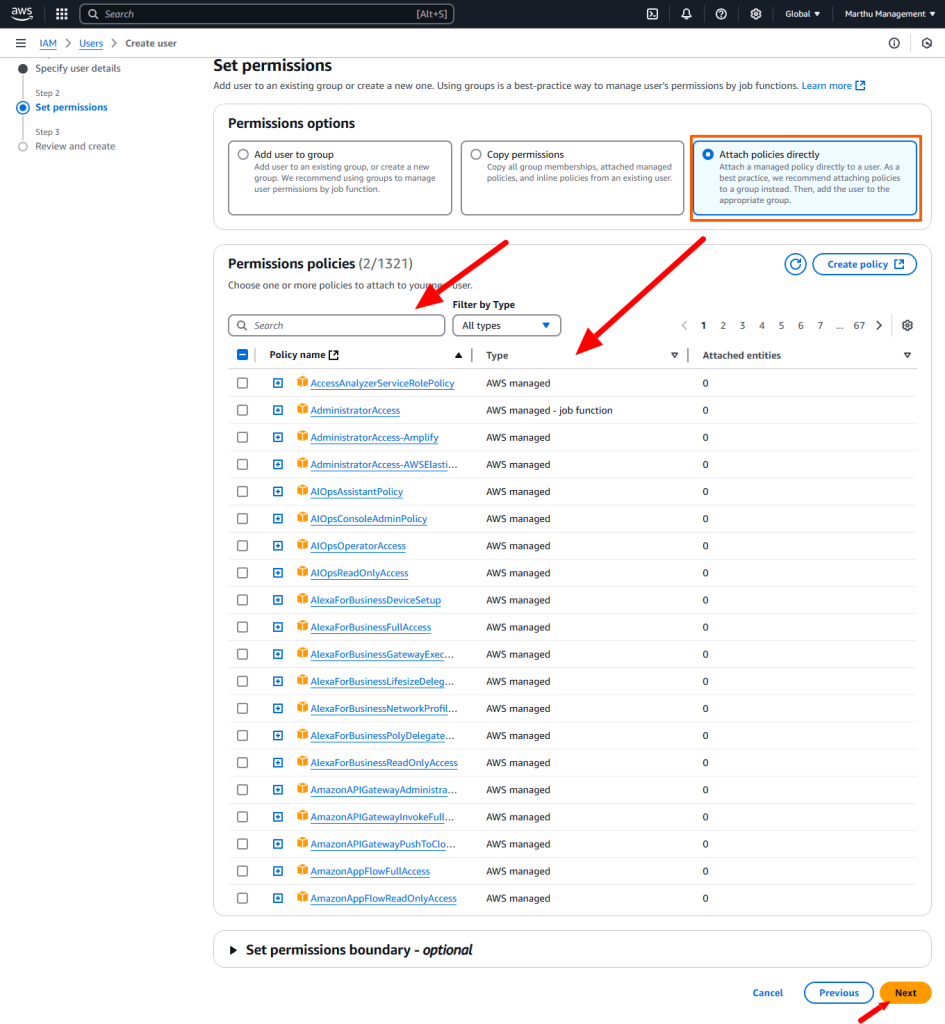
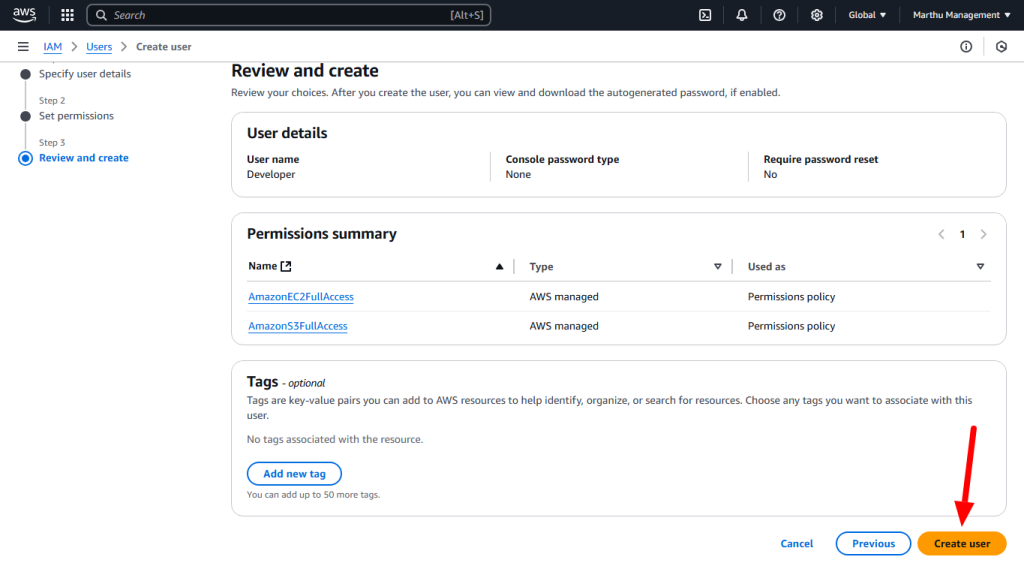
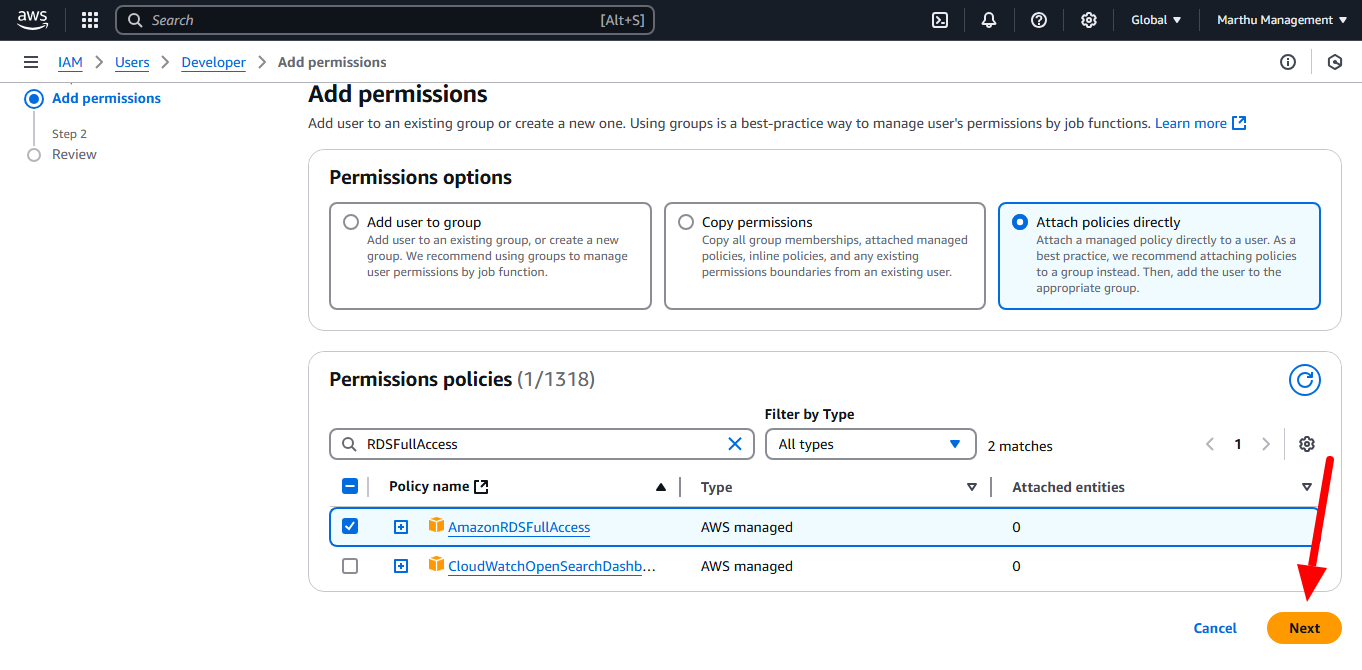
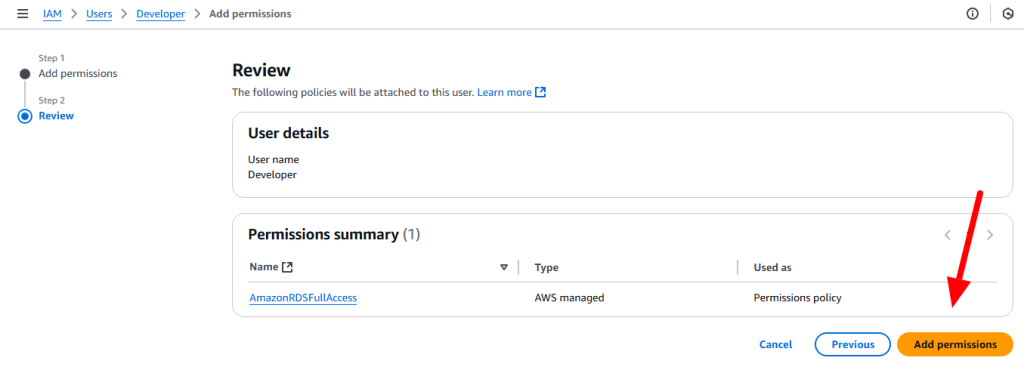
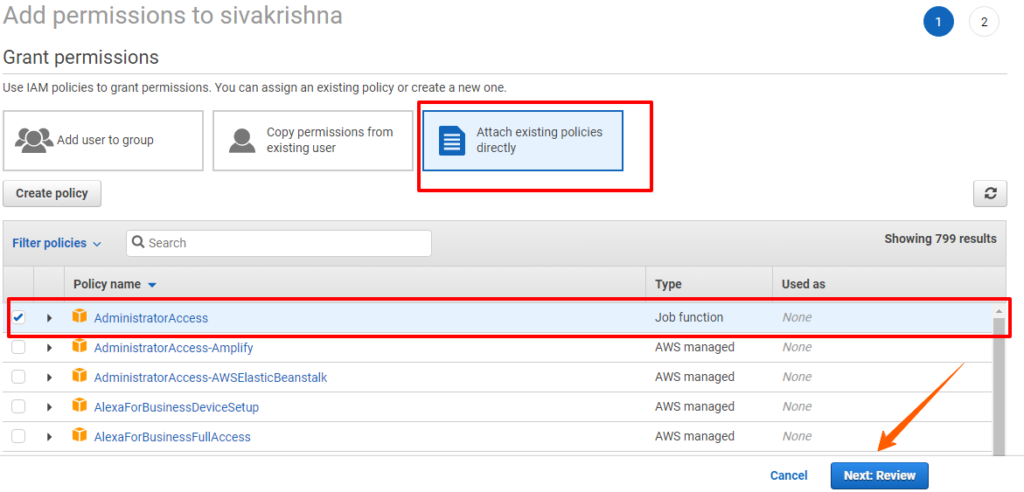
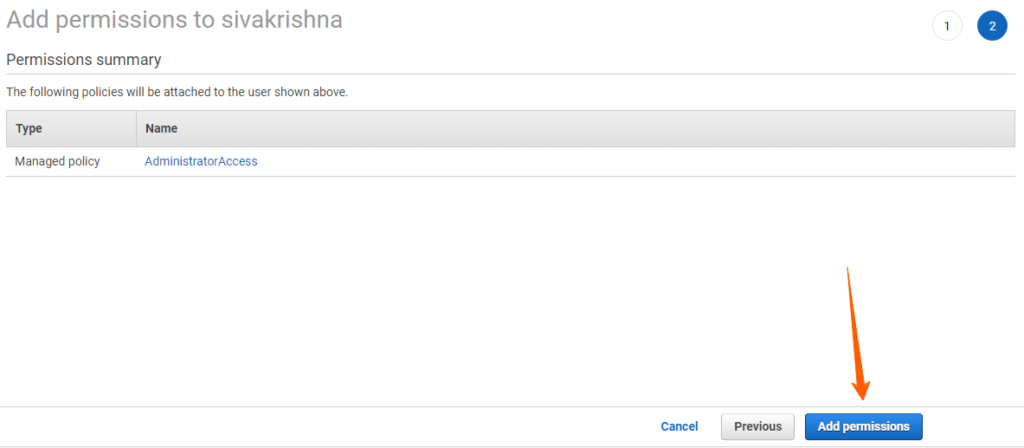
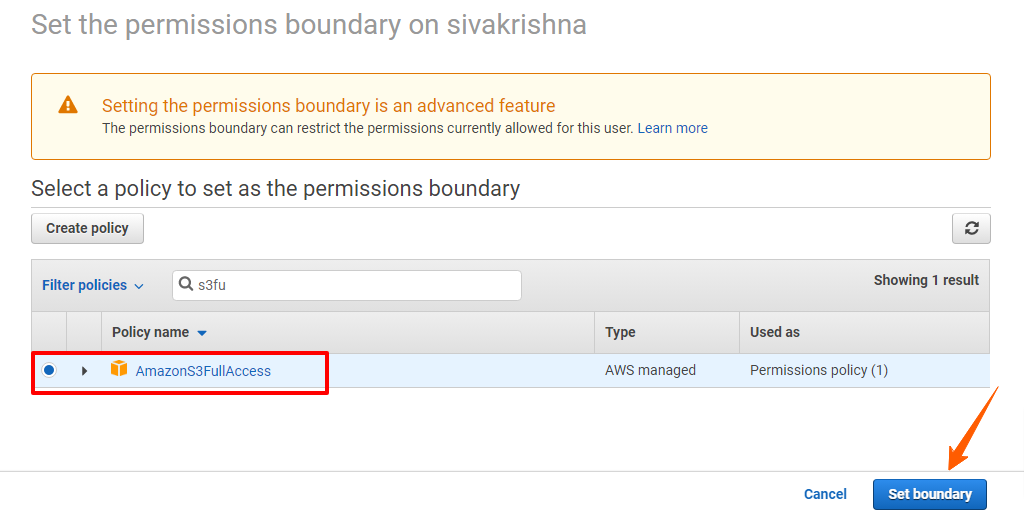
Policy: A policy is a document with a set of rules, having one or more statements. Each policy grants a specific set of permissions and can be attached to any of the IAM identities users, groups, and roles. Policies are always written in JSON or YAML format and each policy has a name.
There are three types of policies are there.
AWS Managed policies: An AWS managed policy is a standalone policy that is created and administered by AWS. Standalone policy means that the policy has its own Amazon Resource Name (ARN) that includes the policy name.
Customer Managed policies: Customer managed policies are standalone identity–based policies that you create and which you can attach to multiple users, groups, or roles in your AWS account. You can manage and create policies using the AWS Management Console, the AWS Command Line Interface (AWS CLI), or the IAM API.
Inline Policies: These policies are directly applied to IAM entities. You use inline policies for a specific objective, which makes them non-reusable.